Starting this week, a massive phishing campaign was launched, apparently by Russian hackers (the sites they used were registered on names of Alexander Kalinin, Alexandr Kvorin, Andrey Morov, and Alexander Petrov with fake addresses of course).
If they get control over someone's account, what they do is that they send private messages to all friends to visit one of the following sites, or alike:
- afoi.ru
- areps.at
- bests.at
- bestspace.be
- brunga.at
- goldbase.be
- indigoline.be
- kirgo.at
- mymarket.be
- nutpic.at
- picoband.be
- ponbon.im
- redbuddy.be
- redfriend.be
- sweeter.be
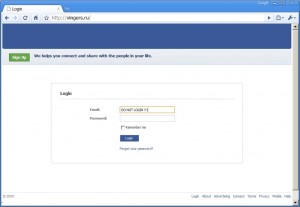
- vingers.ru
- whiteflash.be
- whitemart.be
- yospace.be
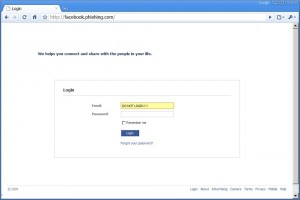
where visitors were asked to "login" again. So this is how they get the passwords.
At the moment, it is unknown how malicious this can turn, but the hackers can potentially hijack other accounts, like e-mail (if the same password is used say for Google or Yahoo mail services), and then even further if they dig more valuable information from someone's virtual portfolio.
So, if trapped - change your password you used on ALL accounts, not only on Facebook. Report it to the site technical team, remove all Facebook applications and take vacations to recover from the stress.
Web administrators, should block the following IP addresses immediately:
- 213.182.197.2
- 211.95.78.98
Short link: http://➸.ws/~G1a2$n


Related Articles
11 users responded in this post
Another useful discussion on this can be found on: http://anshprat.wordpress.com/2009/05/21/areps-at-kirgo-at-phishing-attacks-on-facebook/
Yet another one, I am wondering when will it stop?
A massive e-mail needs to be sent out to all Facebookers.
Maybe Mark Zuckerberg should be focusing more on security than on IPO. After this attack, the latter will be a failure anyway.
Indeed, Facebook should notify all users about this issue. It looks like they cannot control it as more and more accounts get sour.
Blocking only .be domains will not help, it can be any domain. They need to trace those guys and punish them for life for doing something nasty like this.
Funny thing is that the phishing sites were so primitive and even had some English misspellings and grammatical errors, and yet, so many people got caught.
An attack of this scale was well organised, used many servers and withstood weeks of Facebook trying to fight back. The only real thing Facebook did – was asking those affected to reset their passwords.
Conspiracy theory goes like this:
Who is interested in putting Facebook down? A competitor? The government? A third party?
An investmet bank, who was advising Facebook on their IPO would earn dozens of millions – so their rival might decided to kill the deal.
Or was it the buyer that is trying to put the price down this way?
Or was it another Al Qaeda attack?
I guess a book will be written about this case in some ten years by a Facebooker or a hacker or both.
For the moment, as they only ask those affected to reset their passwords it is not very effective. They cure the wrong wound.
Well, Facebook is trying not to lose its face. Let’s see what impact this case will have on their books.
One can only wonder, if the past attack had to do anything with this private placement to reduce the price for some 33 per cent.
In any case, even with optimistic 100 million user accounts, adjusting for all duplicate, spam, inactive ones, let’s say Facebook has 1 million of active users. Even if those generate $100 dollars of revenue each a year – even by applying a multiple of (x 10) this all give a valuation of $1 billion.
Call me sceptical, but I refused to believe in Skype valuation by eBay of $2 billion. Two years later – I am certain.ly not the one to bite my elbows.
All those Facebook investors: good luck!
Those domains were not cheap. smile.be went for 2,000 EUR on SEDO last month.
There is another attack is currently going on. Off-facebook, just a massive spam wave. They sent messages like:
So, do not click on this scam mailing!
A big scam attack is now out, beware: http://www.avertlabs.com/research/blog/index.php/2010/03/17/facebook-suffers-password-reset-scam/?utm_source=twitterfeed&utm_medium=twitter&utm_campaign=Feed%3A+McafeeAvertLabsBlog+%28McAfee+Avert+Labs+Blog%29&utm_content=FaceBook
Another trace of Russian hackers: http://hi-tech.mail.ru/news/misc/russina_hack_socset.html